Due to recent developments in device technologies and extensive access to Internet, a wide range of commercial and governmental activities are carried out over Internet networks. Continuously increasing number of computers and intelligent devices are connected over sub and wide area networks over the Internet. However, due to excessive usage of Internet for both commercial and governmental activities, these networks are constantly under cyber attacks, which progressively improve as the attackers become more sophisticated and better funded. Although firewalls and cryptography technologies are improving and widely used in the current architectures, it is apparent that the cyber attacks will continue to danger Internet networks and improve in time. Hence in addition to these prevention measures, governments and big commercial enterprises are increasingly investing into cyber attack detection systems.
As shown by recently publicized cyber attacks (such as the ones directed against Estonia in 2007), the classical cyber attack detection systems such as SNORT, BRO and IBMQRadar IDS are less than adequate to detect the ever sophisticated cyber threats. These classical methods, which are signature based and perform detection based on their repository of historical attacks, drastically fail since cyber attackers constantly update and optimize their attacks to avoid detection by such fixed and rigid systems. To remedy these problems, anomaly based intrusion detection systems are recently introduced to catch both historical and new ‘zero day’ attacks. However, although the anomaly based cyber attack detection systems provide certain improvements over the classical signature based methods, they are not as widely used since (a) the Internet traffic is highly erratic and hard to model, (b) an event which is considered as normal in the past can be considered as anomaly in the future, and vise versa, (c) the definition of anomaly may change not in time but also from user to user, e.g., the activities of system administrators usually seem highly unusual. Hence due to these difficulties most of the current state of the art anomaly based cyber attack detection systems have high false alarm rates, which significantly deter their usage in real life applications.
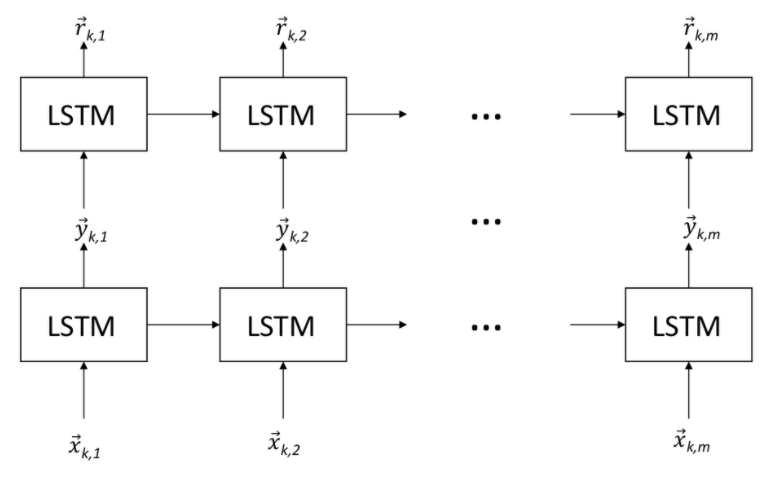
As the first time in the literature, we introduce cyber attack detection algorithms over Internet network loads based on deep recurrent neural networks and Support Vector Machines. The introduced algorithms process the network loads in real time to provide anomaly detection. The algorithms are generic such that they can process network loads in different levels including packet, request, connection or session levels, and can be used in different applications such as ın HTTP, FTP, SMTP etc. To this end, as the first time in the literature, we (1) design autoencoders to extract semantically rich feature vectors from sequentially observed network loads using recurrent neural network architectures, (2) construct anomaly detection algorithms based on deep recurrent neural networks and Support Vector Machines, which are jointly optimized to give the optimal detection performance under any false alarm rate, (3) develop deep learning software architectures and design methodologies incorporating computational cost as an optimization parameter for cyber security applications.
Sample publications:
T. Ergen and S. S. Kozat, “Unsupervised Anomaly Detection with LSTM Neural Networks,” IEEE Transactions on Neural Networks and Learning Systems, 2019.
T. Ergen, A. H. Mirza and S. S. Kozat, “Energy Efficient LSTM Networks for Online Learning,” IEEE Transactions on Neural Networks and Learning Systems, Accepted, 2019.
H. Gokcesu and S. S. Kozat, “Online Anomaly Detection with Minimax Optimal Density Estimation in Nonstationary Environments,” IEEE Transactions on Signal Processing, vol. 66, iss. 5, pp. 1213-1227, 2018.